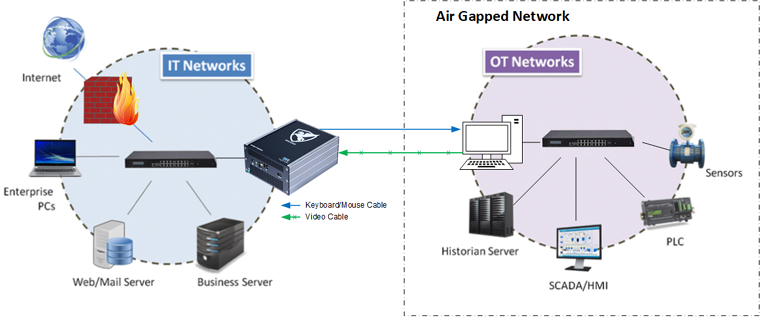
PEGASUS is best suited for customers with the highest cybersecurity requirements and it allows accessing computers that are part of an air-gapped network without breaking the air-gap.
PEGASUS is provided with built-in HDMI output, Ethernet port and two USB 2.0 ports. The USB ports can be used for connecting keyboard and mouse to PEGASUS, for PEGASUS configuration, or for connecting the external network adapters provided.
PEGASUS features a micro-USB port to connect PEGASUS keyboard and mouse commands to target machine. It also features HDMI and DVI inputs to capture the target machine desktop display. VGA input is also available by using the provided VGA to DVI converter.
PEGASUS enclosure is made of durable aluminum and is designed as a faraday cage to filter any EMI that can affect its functionality or used to bypass the isolation between it and the target machine. It also features Key-Rex® screws from BRYCE™ Security Fasteners, the most secured tamper-proof screws in the world. Same screws are used in the most security demanding applications like nuclear, military and museums. This drops the possibility of a successful booby trapping or manipulation of PEGASUS internal components to 6.4e-23%

PEGASUS features extremely strong, hardware locked and time-based double authentication that is virtually impossible to crack using the most powerful quantum computers. Without successful authentication between PEGASUS and the target machine no sessions can be established.
NIRA (Native Interface Remote Access)
The technology utilizes the same native signals used by a computer to dynamically interface with humans.
Basic dynamic human-computer interface:
A computer provides visual dynamic output on a display.
A human provides dynamic input and command to a computer using Keyboard and/or a tracking device.
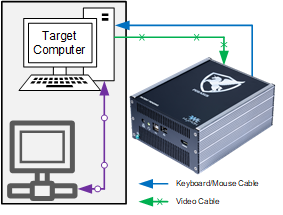
PEGASUS has two connections with the Target Computer:
Video Connection, same as the Target computer would send to any display.
Keyboard and Mouse connection, same as any other keyboard and mouse.
Neither connection would allow any networking, file transfer, or any data transfer between the target computer and PEGASUS other than the keyboard/tracking device commands and the video stream of the target desktop, resulting in effectively maintaining the air-gapping between the two networks.
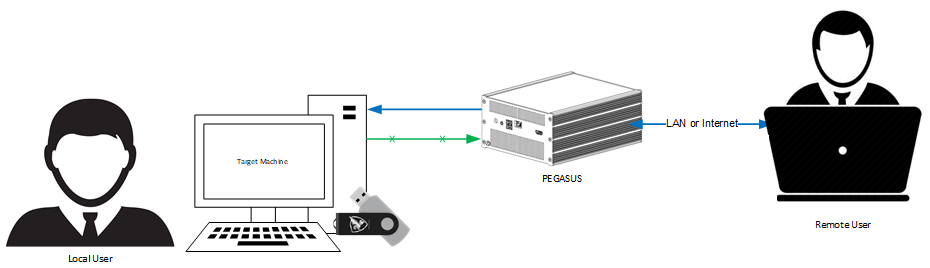
Below is an example of a typical setup for a remote desktop session using PEGASUS:
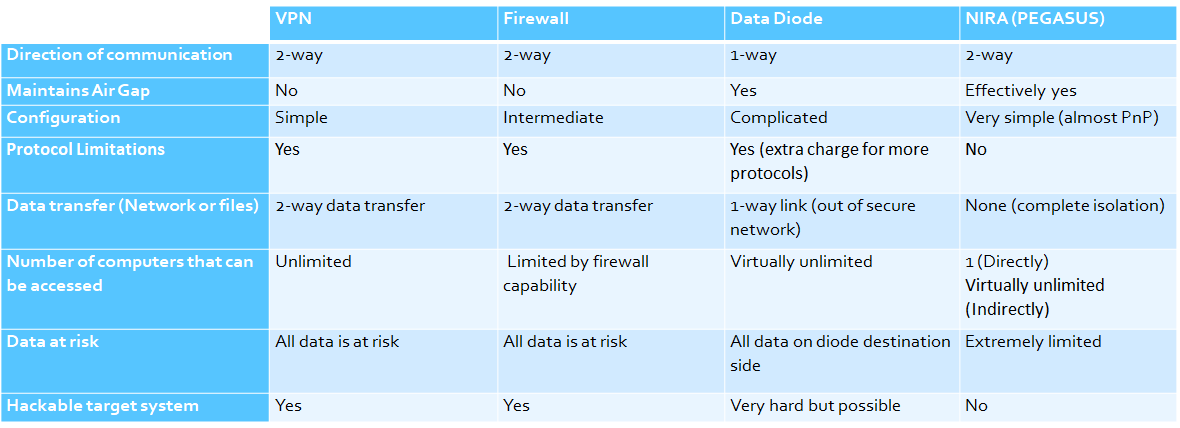
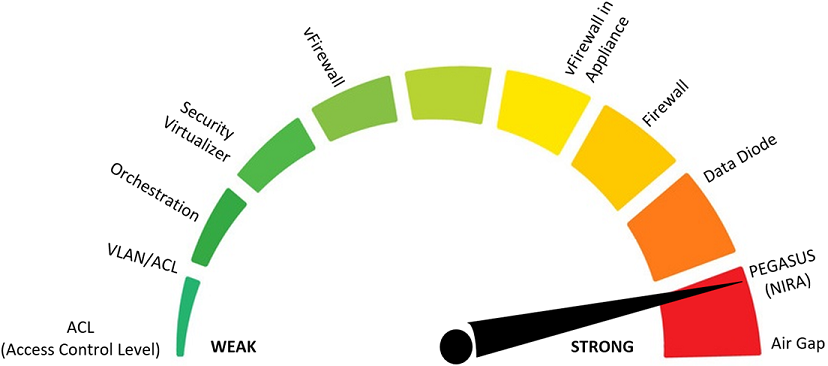
Comparison between some of the most common cybersecurity solutions and PEGASUS (NIRA)
Comparison between PEGASUS (NIRA) and KVM Over IP switches
Due to frequent questions asking what is the difference between PEGASUS and KVM Over IP switches, we have prepared this comparison for clarification.